OSCP PREP BOX 12: HtB Access
Today we’re taking on Access, which is an Easy Windows machine on Hack the Box. To start off, we’ll run our default nmap scan which shows we have 3 ports open.
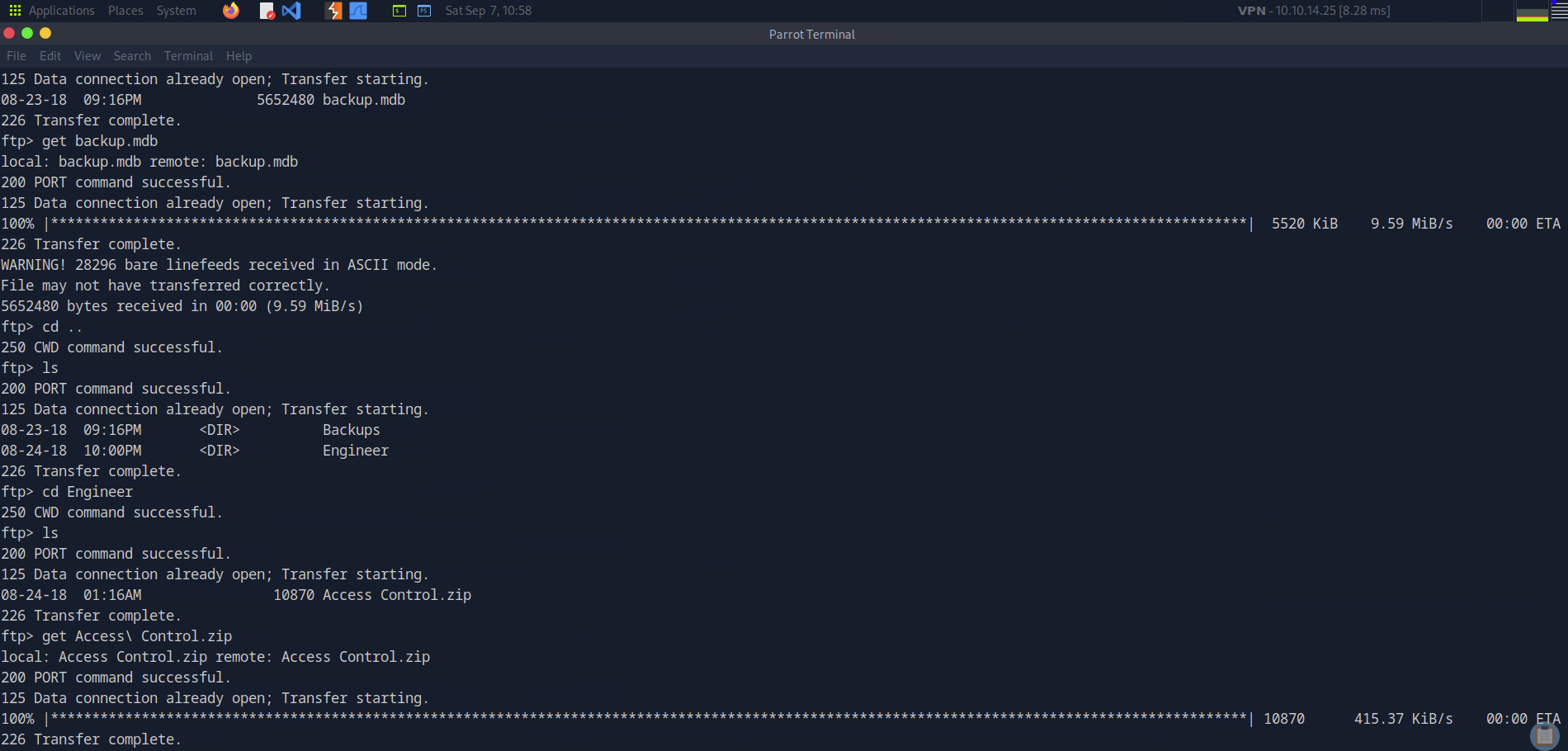
Our default script scan shows that we have anonymous login allowed for the FTP server, so let’s pop into that and see what files we can look at. Off the bat we have two directories, one backup directory and one Engineers directory which contains a zip file. I downloaded the files from both directories using the get command.
Back on our Kali box, I tried opening the zip file but it’s password protected. There are ways to brute force these or decrypt them, but I’ll leave it be for now. Maybe we can find credentials elsewhere. For now, just taking note of that.
The other file is a backup.mdb file. I have never seen mdb files, but in Googling it, it’s a Microsoft Access Database File (literally Microsoft Database (mdb)). I google’d what Linux-based applications we can use to open this file and LibreOffice Calc came up, so let’s go with that. We can see off the bat that it’s not entirely handled by LibreOffice in that we have a lot of unknown characters.
I started by trying to scroll through but it was really unwieldy and several thousand lines long.. So instead I just started searching keywords like password, admin, username, etc. and conveniently, all of them pointed to one line, 631. In going through this line, we can see there’s a string “access4u@security” before the words admin. Let’s give that a shot for the mdb file and for the telnet.
It does not work for telnet but it does work for the pst file contained in the zip! Now let’s see how to open a pst file. Success! Let’s extract that and go back to the command line. Now we have ‘Access Control.pst’ We can now use a binary called readpst to open the pst file which now gives a file, Access Control.mbox. I found this article which made this whole process really easy to understand since I’ve never worked with these files before. https://theevilbit.blogspot.com/2013/01/backtrack-forensics-convert-pst-mail.html
But, I found that using -r to make it a directory made the whole file read easier, so the command you’d run would be readpst -r ‘Access Control.pst’
This would then create a directory and you can cat out the .mbox file from there!
Luckily this one is much shorter for us to skim through..
We can see in the body of the email we now get credentials for the security account which is 4Cc3ssC0ntr0ller. I tried to use this for FTP and it didn’t work, so let’s try telnet. Success!
From here we get our user flag on the desktop of the security user.
On the account, we can see we only have two users, the security user and the Administrator account (plus Public).
Let’s do some enumeration. I started by seeing who we could access as far as users. Administrator was denied, obviously, and there was nothing else really in the security directory. I then checked Public where I found an lnk file:
I Google’d Lnk files and saw that they were basically like binary shortcuts. I then just google’d lnk file exploits and found you could obtain RCE through them! The reason I poked this so far was because to find a file like this in Public is extremely unique and likely there for a reason..
I then copied the text from that file and brought it over to vim and filtered out all the unknown characters to make it more readable.
John Hammond actually did a nice YouTube video about lnk files and making them malicious. The reason we’re able to make them malicious is because it ends up basically being a PATH abuse type vulnerability.
So we can see that the executable executes Access.exe. So if we replace Access.exe with an msfvenom payload and then trigger the lnk file, we could get RCE as root. Let’s give it a shot. Failed.. that didn’t work. I ended up running icacls on Access.exe and even though we can write to ZKAccess3.5, we only have read and execute permissions over Access.exe.
So in researching runas, we can use that basically like we would sudo privs on linux. I kept trying to get a shell, but struggled to pop one. I was able to get file exposure though using stored credentials: runas /user:access\Administrator /savecred "cmd /c type C:\Users\Administrator\Desktop\root.txt > C:\Users\security\Desktop\root.txt"